1. Intro
This is the story of a guy we are going to call.. hum.. Bob. Bob think he is smart. He scams people via internet, abusing foreign hosting and redacted for privacy whois domains.
But before I tell you Bob's history, we are going to need a bit of context. And here's is something about brazilians: They are good people (most of them). And they love a discount. Also, they love auctions, cuz well, auctions are cool. And you can, eventually, get good prices. To make matters worse, in Brazil, it's common for the government to make auctions of impounded vehicles and other things that were seized in operations. You can see where I'm going with this, don't you?
Exactly. Bob likes to scam people by creating fake government auction websites. And private ones, too. He takes pictures from yards full of cars (probably from some legit company) and then he pretends there is an auction, with really good prices. He sets up his fake process really well, so people have to go through a validation before they can buy anything (yeah, exactly, before they are scammed). And then, only then, he allows the victims to make their bids and transfer money if they are declared (fake) winners.
Of course, the whole thing is a facade and when Bob gets the money he wanted, he's gone. Domain? Offline. URL? Deactivated. Money? Probably spent on something nice for himself. With all the delicious protection from private domain registration services, and hosting on countries were Brazilian authorities can't subpoena for anything. To rely on some governments cooperation in those cases is.. lets say.. a bit optimistic.
Bob is such a smart guy. Untouchable. He is sure he is smarter than everybody else. He's sure his money is well deserved. A true Danny Ocean of online fraudsters.
Well, let's see about that.
2. Who(IS)
You don't need to be freakin' Sherlock Holmes to know you should start with the basics: Whois and crt.sh to check what you can know about the domain and it's SSL certificates. In this case, let's focus on Whois first and see where that can take us. Our target: Bob's most known website, XXXXXXXXXXXleiloes-br.com
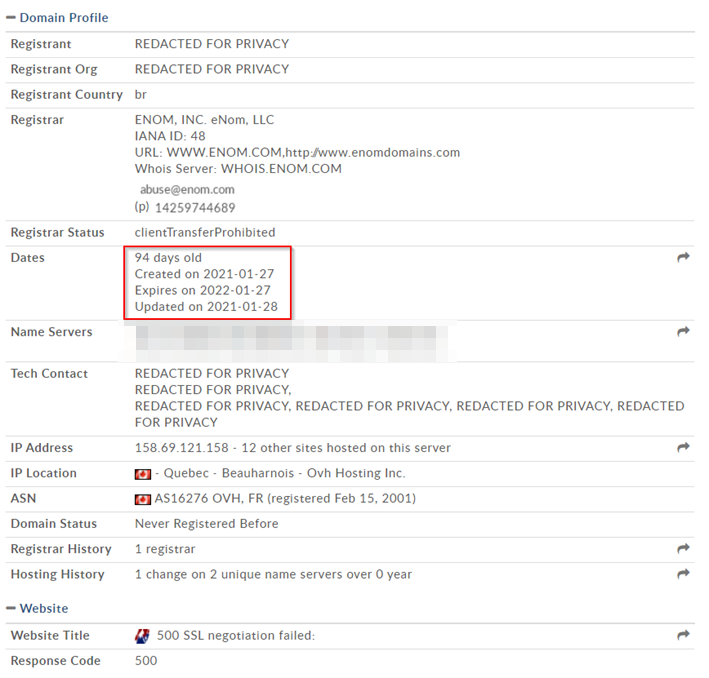
Figure 1 - Whois basic information
Redacted for privacy. Of course, Bob is no spring chicken. A seasoned warrior of life like himself would not make such a mistake of revealing who he is so easily, right?
But we can already start to have some fun. The domain is 94 days old at the time of the screenshot (yes, these are tales of the past), but would you look at this:
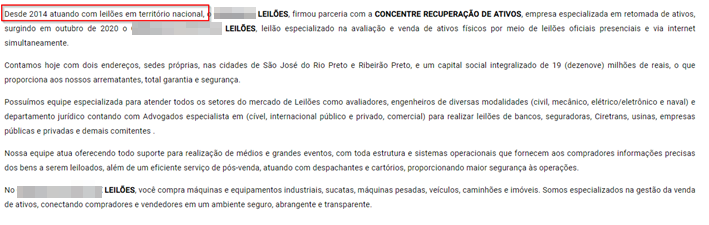
Figure 2 - ABOUT US section of the website
To translate the part highlighted in red: It says the "company" is on the market in the whole national territory (of Brazil) since 2014. But the domain was registered only in 2021. Of course that would be a surprise... if we did not knew better.
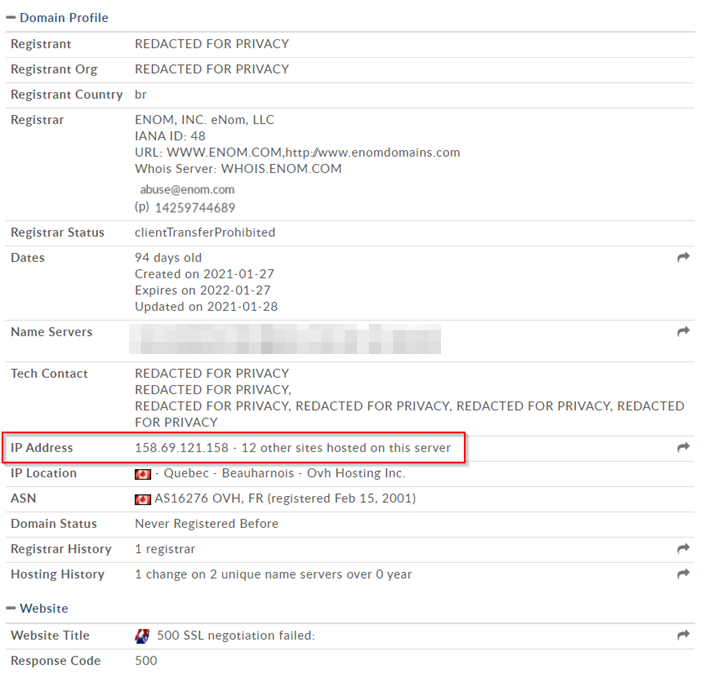
Figure 3 - IP address datapoint
Well, seems like Bob is not satisfied with only one website. Let's check this for a bit:
Figure 4 - Other domains associated to the original IP address
Interesting.
In good ol' times, BING used to let you search by IP (bring it back plz!!!). Back then, you could search for the target IP address and find the following domains as well:
- XXXXXleiloes-br.com
- XXXXleilaodeXXXXX-br.com
- leilaoXXXXretomados-br.com
- XXXXXautoleilao-br.com
- leilaogrupoXXXXX.com
- pXXXXXleiloes-br.com
Bob, Bob, Bob. You're a greedy one, don't you?
Checking these domains, is also a lot of fun. Same template, just different names and color scheme. Old Bob is not wasting any time with new designs:
Figures 5 to 8 - Checking out the websites similar design
Btw, "Leilão" means "Auction" in Portuguese.
3. CMS
At this stage, it's really relevant to pinpoint what is our target running. Is it PHP? Flask? Nginx or Apache? Wordpress? Any information will be relevant for you to enumerate whatever vulnerabilities or extra information about your target.
Of course you can always just read the HTTP readers manually, but this is kinda boring and a last resource. Starting with easier things, like Netcraft Site Report Tool will tell us that this guy is running Wordpress.
I mean, this makes total sense. The guy is too lazy to work. He will be too lazy to design a website from scratch, and there is nothing as easy as running Wordpress.
CMS, by the way, means "Content Management System", and Wordpress is one of those "CMS" options in the market. Most of the web runs Wordpress, so I strongly suggest you get familiar with it. It's very likely that, on your journey in this field, this knowledge will be useful someday.
And as I'm the kind of person to live by the advice I share with others, I did get familiar with Wordpress. And doing so, I discovered that one of the most common misconfigurations is that people don't set the wp-content/uploads folder private. This makes it easy for you to see what the owner of the site is storing under the hood. It also makes it way easier for you to just use some WGET magic to download and batch analyze the whole thing:
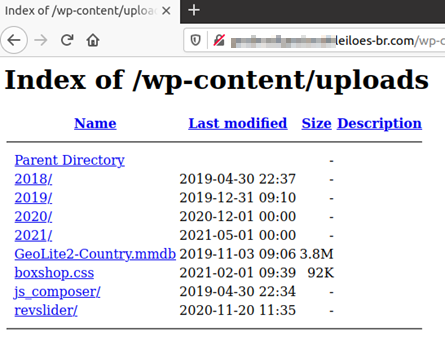
Figure 9 - Uploads Directory
Word of advice: Don't leave your uploads directory open at night. Somebody might come in to check it out.
4. WGET
As per the great repository of human knowledge called Wikipedia:
"GNU Wget (or just Wget, formerly Geturl, also written as its package name, wget) is a computer program that retrieves content from web servers. It is part of the GNU Project. Its name derives from "World Wide Web" and "get." It supports downloading via HTTP, HTTPS, and FTP."
That is what it is. But what really matters is what you can do with it. And here's a tip:
wget --recursive --page-requisites --convert-links --no-parent --reject=*.mp4,*.mkv,*.avi NAMEOFYOURTARGET.COM
This mouthful of a command will allow you to download the entirety of a website (or a given directory and its subdirectories) without taking too much time downloading videos (if you want the videos just remove the --reject part) for you to preserve the data (in case the website is taken offline) and also to make it easier for you to analyze it.
You are welcome.
Of course, I did download the entirety of the /uploads from his server. Let's see what interesting findings awaits us.
5. The Uploads
I'll let the images speak for themselves.
Figures 10 to 14 - Victims and "the next endeavors"
As smart as Bob is, he tricks people into believing he's got a legal process, full of redtape. He even demanded people sent him copies of their ID's, as well as pictures holding the document. There were hundreds more in the /uploads directory, but there is no need to list them here. Also, we can see he was already setting up other new auction websites.
And for the next trick...
6. EXIF Magic
exiftool -r ./website_downloaded_folder > exifdata.txt
The above command will use the magnific exiftool (apt-get install exiftool if you are one of the blessed debian-based linux adepts like myself) to extract all the metadata from every single file that you downloaded from the website (stored in our dear website_downloaded_folder) and direct the output to our exifdata.txt for analysis. (Yes, you can exif a single file at a time. If you like to suffer, of course.)
And just like that I have all the metadata from his uploads folder stored in a text file, for my viewing pleasure.
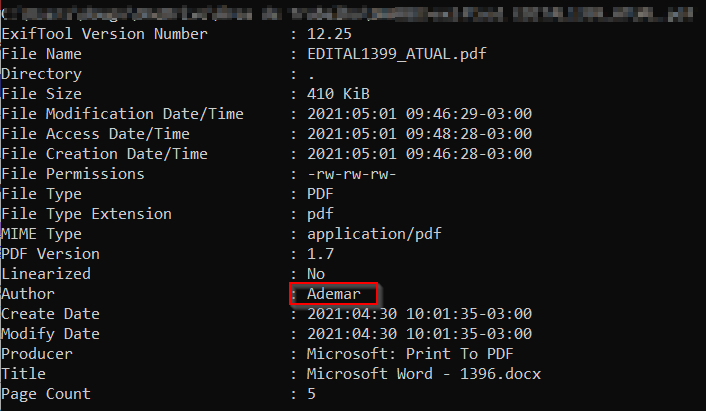
Figure 15 - Hello, friend.
Well, well, well. Two hypotheses arise:
- 1) Bob is really cautious, and replaced his real name for "Ademar" (a common name in Brazil) to throw me off his tail;
- 2) Bob forgot to delete the metadata from this file.
As a big believer in Occam's Razor, I gotta check this name a bit more.
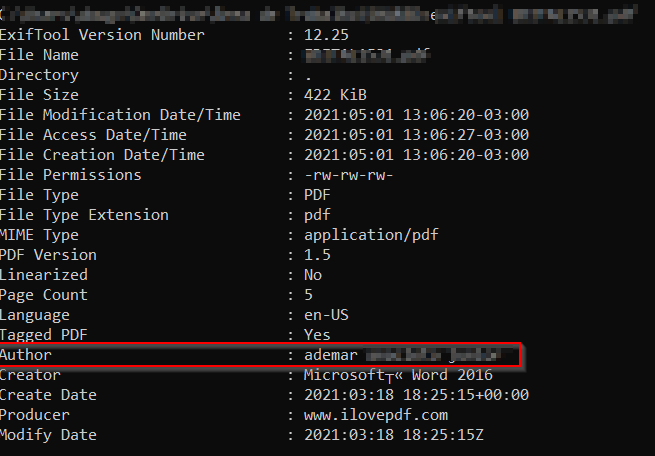
Figure 16 - Hello again, friend.
One more file with this "Ademar" name. Or alias. We'll see.
Figure 17 - Wait, what?
Either Bob is really smart and invented a full name to throw us off or we've just got really relevant middle and last names. "Ademar AXXXXXX JXXXXXX". Let's dive into it.
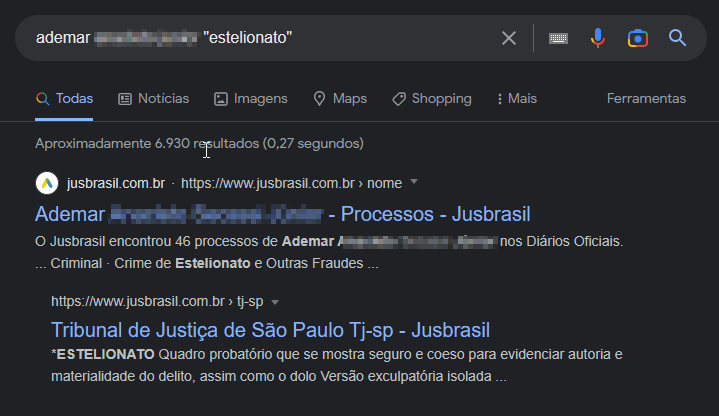
Figure 18 - Embezzlement all around
This is as simple as it gets. Google'd the name of our suspect + the word "estelionato" ("embezzlement" in portuguese).
And... that little googling shows some really interesting stuff. The image presents 46 lawsuits against somebody called "Ademar AXXXXX SXXXX JXXXXXXX" in a state court in Brazil, for embezzlement and other frauds. A closer analysis of the lawsuits (wich I will not share here) shows they were a little less sofisticated when compared to his new "way of life" defrauding people over the web. Seems like he learned a thing or two after getting caught the first.. 46 times.
It's not yet the defacto proof we want, but we've just got a guy with the same name contained in the PDF file metadata involved in similar frauds, and now we even have an extra middle name. We just have to keep forging ahead, amirite?
7. With a little help of my friends
I know, i know, it could be that this "lawsuit Ademar" is not our Ademar/Bob. It could be a coincidence, and this guy, with 46 lawsuits for embezzlement, is not the guy embezzling people this time. It could be that, in this Matrix, there are two Ademar's with the same name doing the same thing. Or, by Occam's Razor, it is the same guy, and well.. in this case, the sun is about to become a little squared for him in the morning.
Once again: I´m not advocating this guy should be arrested based only in the evidence above. But sure as hell we got a lot far from the "REDACTED FOR PRIVACY" with just a bit of Googlin' and good old WGET magic.
In cases like this, when you get almost all the proof to build a criminal case from your laptop while drinking two mugs of coffe, you might feel the urge to send an e-mail to some friends, and maybe those friends have badges and access to some really cool government databases. Maybe they are even willing to run a really efficient procedure called "search and seizure". And if you were right all along, Bob might end up being arrested for his crimes.
Spoiler alert: That e-mail was sent. And "lawsuit Ademar" was indeed confirmed as our Bob.
8. Final Thoughts
If there is a lesson within this post, is that we must not disrespect the basics. Specially when you are beggining. You can do stuff as a white belt.
In the other hand, the veterans also must have in mind that it's not because you can do some pilot shit that you should do it everytime. Sometimes the basics are plenty. In the end, creativity rules all... even if you are a master in the jedi ways, the basic stuff will get you by.
Bob was not caught because I used some Wordpress buffer overflow shenaningans. No directory traversal, XXE injection, Blind SQL injection, HTTP Smuggling, nothing.
He went down because of a misconfiguration, a bit of patience and very simple metadata analysis.
What would you think if I sang out of tune?
Would you stand up and walk out on me?
Lend me your ears and I'll sing you a song
And I'll try not to sing out of key
Oh, I get by with a little help from my friends
Mm, I get high with a little help from my friends
Mm, gonna try with a little help from my friends
PSA: No endangered VPS species were harmed in the making of this post.